| Förstå och hantera tillit för paket | ||
|---|---|---|
 | Hantera paket |  |
apt's ability to access multiple package sources leads to a potential
security vulnerability. Suppose you add an archive of packages published by
Joe Random Hacker to your sources.list file in order to
install Joe's gargleblast package. It is possible,
however, that -- unbeknownst to you -- Joe's archive also contains his own
“customized” versions of packages such as
libc6 and ssh...versions
that steal your private information or open backdoors on your system! If
these packages have higher version numbers than the legitimate Debian
packages, apt will blithely install them on your system during your next
upgrade, allowing Joe to do his dirty work undetected. Joe could also break
into your mirror of the Debian archives and replace the legitimate software
with his doctored version.
Luckily, newer versions of apt and aptitude, such as the version
documented in this manual, have built-in safeguards to help defeat this type
of attack. apt uses strong security mechanisms based on the popular
GPG encryption software to verify
that the packages being distributed from the official Debian mirrors are the
same packages that were uploaded by the Debian developers. aptitude will
then warn you if you attempt to install a package from a non-Debian source,
or if you attempt to upgrade a package that was installed from a Debian
source to a version that came from a non-Debian source.
![[Varning]](images/warning.png) | Varning |
|---|---|
The security mechanisms in Ensuring that you only install software from a trusted source will give you an important degree of protection against malicious packages, but it cannot eliminate all the risks inherent in installing software. |
apt allows the administrator of an archive to provide a
signature of the archive's index. This signature,
which (for all practical purposes) cannot be forged, indicates that the
package files listed in the index are the same files that the administrator
intended to place in the archive: ie, that the contents of the archive have
not been tampered with since it was created.[9] The signature can be validated by checking that it corresponds
to the administrator's public key. The public key of
the Debian archive is distributed with apt, typically on your Debian CD.
When aptitude downloads an archive index, it will check whether the index is properly signed. If it is unsigned, aptitude will not trust package files from that archive. (see below for information on what this means) If it has a signature but the signature is incorrect or cannot be verified, a warning will be printed and aptitude will refuse to trust packages from that archive.
Later, when you perform an install run, aptitude will check whether the packages are from trusted sources. If an untrusted package is being installed, or a package is being upgraded from a trusted to an untrusted version, a warning will be displayed and you will have the opportunity to abort the download:
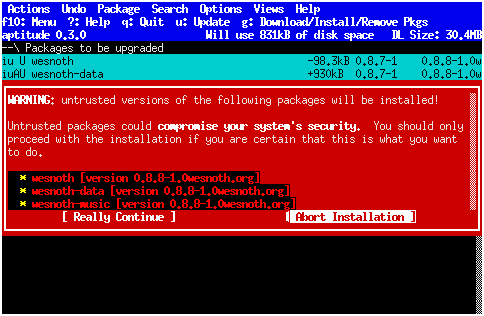 |
You might find it useful to allow apt to trust additional archives,
besides the main Debian archive. For each archive that you want to trust,
you will have to acquire the public key that is used to sign the archive's
package index. This is typically a text file whose name ends in
.asc; it might be provided by the site administrator or
downloadable from a public keyserver. For more information on what public
keys are and how to get them, see the GPG
web page.
The list of keys that apt will trust is stored in the keyring
file /etc/apt/trusted.gpg. Once you have
the GPG key, you can add it to this file by executing the command
gpg --no-default-keyring --keyring /etc/apt/trusted.gpg --import
newkey.asc. aptitude will then trust
any archive that is signed with the key contained in
newkey.asc.
![[Varning]](images/warning.png) | Varning |
|---|---|
Once an archive's key has been added to the APT keyring, it will be trusted just as much as the main Debian mirrors themselves! You should only do this if you are very confident that the key you are adding is correct and that the person who holds the key is trustworthy and competent. |
[9] As noted above, it does not indicate that the packages in the archive are secure, or even non-malicious; it merely shows that they are genuine.